Windows Registry
Registry Keys and Values
Q: Is there an easy way to see what registry keys are accessed or modified by every process or dll upon execution or during runtime?
Yes, there are two relatively easy methods to check for this activity, Windows Sysinternals Process Monitor and Windows Performance Analyzer and Recorder. Windows Sysinternals Process Monitor is best used during realtime analysis, launching a process or restarting a service whereas Windows Performance Analyzer and Recorder also allows you to capture key information during the boot process.
Findings and Analysis
Process Monitor
- Download Process Monitor - https://docs.microsoft.com/en-us/sysinternals/downloads/procmon
- Run as admin and press OK to apply the default filter
- In the navigation bar ensure that only Show Registry Activity button is selected.
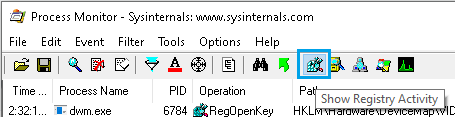
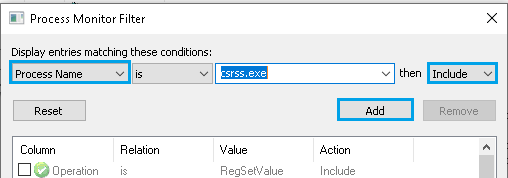
- Use the filtering options Filter Menu -> Filter -> Add to narrow down on the process of interest then press OK. You can also filter on the type of Registry I/O activity once you have a better idea of what you're looking for.
Windows Performance Analyzer and Recorder
- Download Windows Assessment and Deployment Kit (Windows ADK) - https://docs.microsoft.com/en-us/windows-hardware/get-started/adk-install
- Only install Windows Performance Analyzer toolset
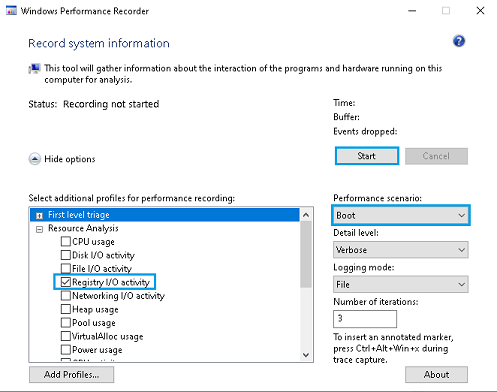
- Open Windows Performance Recorder, select Performance Scenario: Boot, or if you want to capture a realtime snapshot then just choose memory or disk. Memory is preferred for short lived performance recording scenarios and disk for longer recording sessions.
- Expand Resource Analysis then ensure to select Registry I/O Activity and if ready, press Start
- Once the restart process is complete use Windows Performance Analyzer to review the recorded information, use the builtin filtering options to limit by process or registry paths.
Q: What are some of the registry keys accessed on boot? Do they reveal potentially hidden registry keys and values?
There's a large amount of registry keys loaded on boot as the registry is intended to persist application and operating system configuration state between uses. There does appear to be many potentially hidden registry keys for drivers and operating system functions based on the attempted access patterns, however most of these are often without documentation so to prove there is any difference may require further research, performance analysis, trial and error. See findings and analysis for more details.
Findings and Analysis
- Using Windows Performance Analyzer and Recorder as described in Is there an easy way to see what registry keys are accessed or modified?, the following key value pairs were only some of the notable identified values during the boot process of my machine.
- AudioSrv
- Desktop Window Manager (dwm)
- Windows OS Supplementary Graphics Drivers Options
- Display Adapter Class
- Network Adapter Class
- Keyboard Class
- Keyboard HID
- Mouse Class
- Mouse HID
- Kernel Velocity
- Multimedia Class Scheduler Service
- NVIDIA Display Driver
- Storage AHCI
- Storage NVME
- Storage TCPIP
- Network Driver Interface Specification (NDIS)